State-of-the-art cybersecurity & compliance
According to the study, 81% of companies were victims of theft of data and IT equipment, digital and analog industrial espionage or sabotage. This also represents an increase from 72 percent.
Without a robust security system in place, you are putting your business at immediate risk. Protect your company’s sensitive data and integrate state-of-the-art cybersecurity with Belzir.
Without a robust security system in place, you are putting your business at immediate risk. Protect your company’s sensitive data and integrate state-of-the-art cybersecurity with Belzir.

Stop Threats Before They Start
Proactively address cybersecurity risks and build a reliable, trustworthy IT infrastructure.
Cybersecurity You Can Trust
Secure your devices, data, and users with integrated protection at every stage—ensuring safe operations at all times.
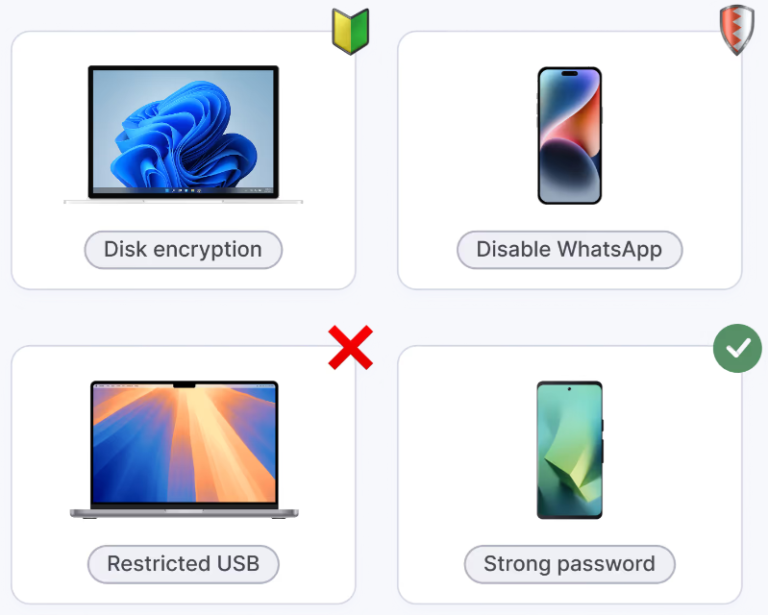
Enforce Security Policies
We help you apply and maintain the right security settings across every device.
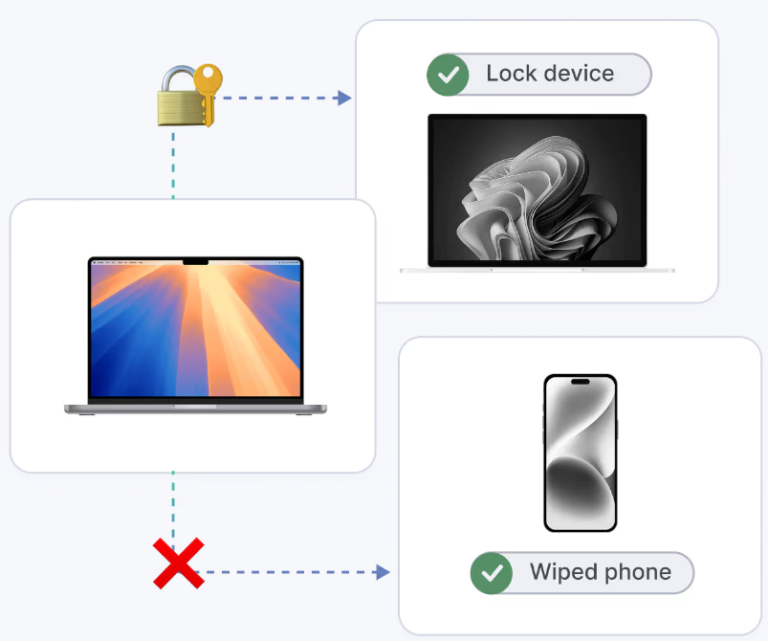
Lock or Wipe Devices Remotely
Lost laptop? No problem. Remotely lock or wipe any device to keep your data and piece of mind protected.
Password Guidelines, Always On
From length to complexity, you set the standards — we make sure your team follows them.


Security Updates, Handled
We make sure every device gets the latest patches and protections without waiting on users.
Go Beyond the Basics with SentinelOne
Want advanced endpoint protection? We integrate with SentinelOne to keep your devices safe from threats in real time. Available as a premium add-on.

Prevent threats from turning into real issues.
Stay one step ahead with automated security that detects and responds before threats turn into incidents.
Prevent threats from turning into real issues.
Stay one step ahead with automated security that detects and responds before threats turn into incidents.
With BELZIR
Modern Protection for Today’s Workforce
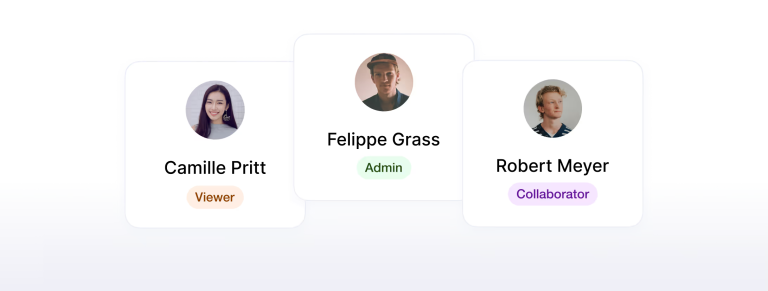
User Permissions that Match Your Team
Whether admins need full control or team members require specific access, you can easily tailor permissions to fit your team's needs.
Set Boundaries That Stick
Limit access to risky sites and unauthorized apps. Your rules, enforced automatically.

Encrypted by Default
Every device is secured with enforced encryption. Sensitive data stays protected.

Certificates for Secure Authentication
Easily push authentication certificates to devices. No manual setup, no user confusion, just secure access from the start.
